3D Printed Nylon, Mirror, Facial Recognition and Detection Algorithms, Genetic algorithms
18 x 26 in each
2013-2015

Data-Mask Installation View at ZKM Karlsruhe for GLOBALE: Infosphere, Sep 2015

Sobek Data-Mask Installation View at ZKM Karlsruhe for GLOBALE: Infosphere, Sep 2015

Zuck Blister Data-Mask Installation View at ZKM Karlsruhe for GLOBALE: Infosphere, Sep 2015
Overview
Data-masks are face masks which were created by reverse engineering facial recognition and detection algorithms. These algorithms were used to guide an evolving system toward the production of human-like faces. These evolved faces were then 3D printed as masks, shadows of human beings as seen by the minds-eye of the machine-organism. This exposes the way the machine, and the surveillance state, view human identity and this makes aspects of these invisible power structures visible.
Data-Masks are animistic deities brought out of the algorithmic-spirit-world of the machine and into our material world, ready to tell us their secrets, or warn us of what's to come.
This work is a continuation of my Masters of Science thesis, which is a theoretical and technical investigation into the form and function of biometric surveillance technology, the mathematical analysis of biological data.
Theoretically, I am concerned with the aggressive overdevelopment of surveillance technology and how this is changing human identity and how humanity interacts with technology. By technology I mean individual instances of technological devices and networked systems like cameras and software, but also what I identify as the 'Technological Other', a global living super-organism of all machines and software. Technically, my specific focus has been in reverse engineering facial recognition, facial detection, and image correlation techniques in order to reveal how they represent human identity.
This research has resulted in the production of a series of 3D printed face masks which were algorithmically evolved to satisfy facial recognition algorithms. It is important to understand that the goal of creating these masks isn't to defeat facial recognition or provide something undetectable, simply covering your face with your hand will do that. Rather, my goal is to show the machine what it's looking for, to hold a mirror up to the all-seeing eye of the digital-panopticon we live in and let it stare back into its own mind.
Data-masks are intended for use in acts of protest, poetry, civil disobedience, and shamanistic ritual by the citizens of our global village as it becomes further blanketed by techno-sphere.
Technical Details
If you would like to know more about how this was done, please refer to my Master's Thesis titled "Data-Masks Biometric Surveillance Masks Evolving in the Gaze of the Technological Other"
Motivations
This work is an act of political protest by means of bringing transparency to the surveillance and biometric techniques used today. These Data-masks give form to an otherwise invisible network of control and identification systems and make their effect on our identities tangible and visible.
"You can't hit what you can't see, you can't grab what you can't touch. You can't critically engage with technoculture and its infrastructure if you're unable to unravel its threads, run your fingers through the seams, visualize its jurisdiction and weigh its influence on everyday life." #Stacktivism
Computer systems built to represent human identities have contained with them many ontological assumptions about what it is to be an individual and what personal identity is. These systems define the human as a "what" ie: that which can be measured, not as a "who" ie: our inner self.
If the state of the art in computer science can produce a unique feature that describes an individual as such, what good does that do the individual if this knowledge is only leveraged against them?
If private citizens personal information, social graphs, and communications are being analyzed then the results should be made available to said persons to empower rather than enslave them. This attitude has become popular in personal fitness but not in communications, biometric identity, or social networks.
"We see the world, not as it is, but as we are" - Talmud
Face Detection Masks

Chronos

Kodama

Zuck-Blister

Sobek

Atë

Void
Face Recognition Masks

Obama

Snowden
Excerpt from M.S. Thesis "Data-Masks Biometric Surveillance Masks Evolving in the Gaze of the Technological Other"
Biometrics and Personal Identity
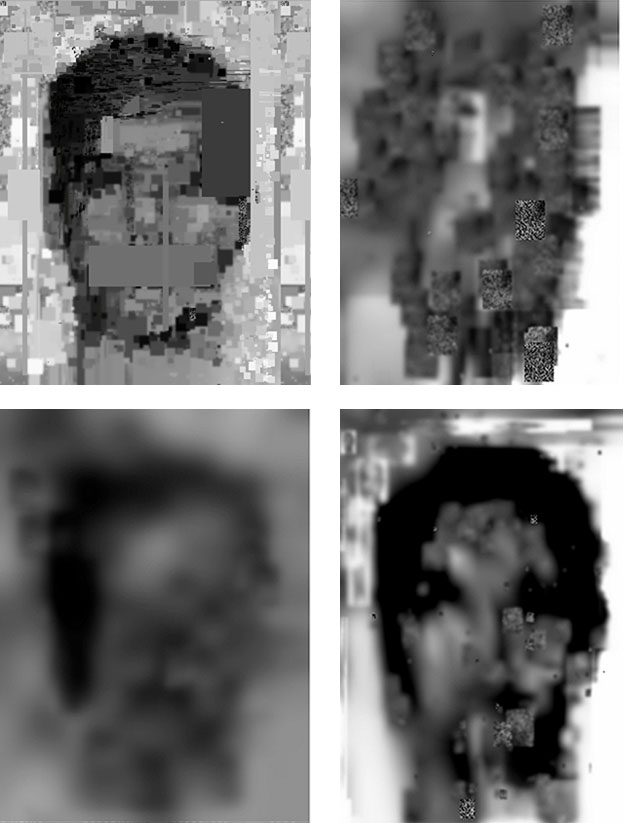
What are we as humans and as individual people? Are we simply a series of statistical probabilities and biometric patterns? Systems of representing human beings identities have contained with them many ontological assumptions about what it is to be an individual and what personal identity is. The previously described surveillance and biometric identification systems define the human as a "what" ie: that which can be measured, not as a "who" ie: our inner self. When human identity is extruded through these instruments of mathematics and computation there is a great reduction how humans are represented.
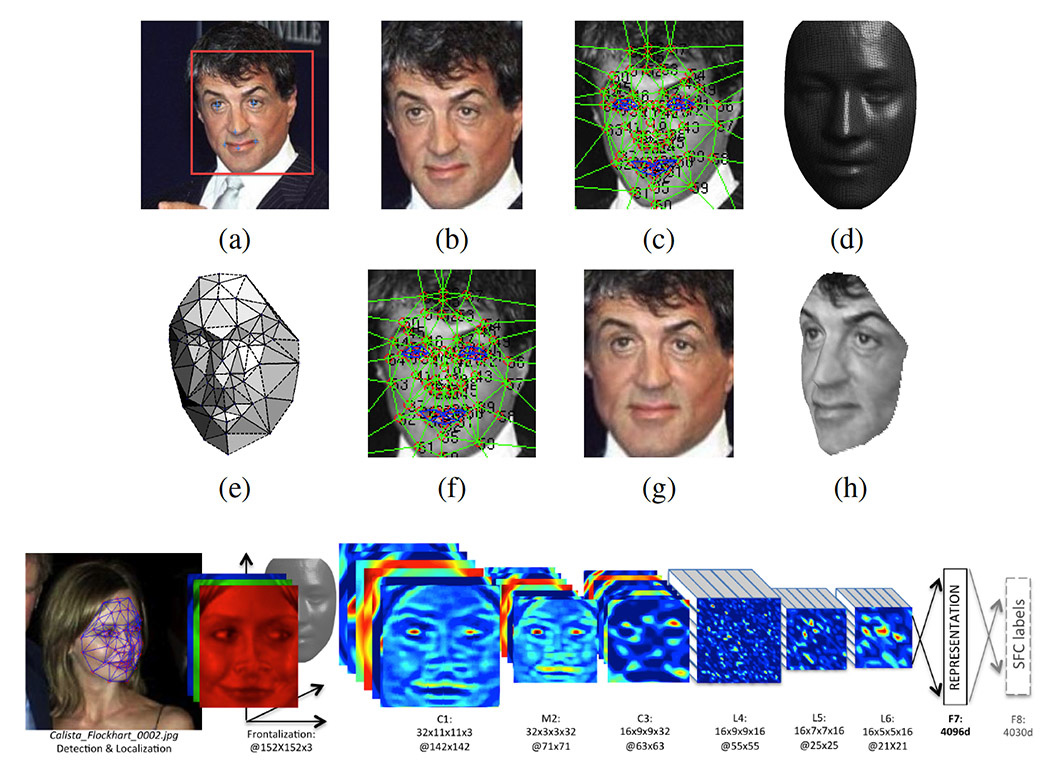
As an example we can look to Facebook's DeepFace system (shown above) of representing human identities as 3D models and statistical features . This is out of necessity and efficiency for computational reasons but the results are disturbing. This is in part due to the visually ghastly disfiguration of the human face and the dismemberment of its features. But also because none of the knowledge gained from this analysis is shared with the individuals analyzed. If the state of the art in computer science can produce a unique feature that describes an individual as such, what good does that do the individual if this knowledge is only leveraged against them?
Biometrics and Surveillance
Biometrics is the measurement and analysis of biological data which can be traced to Charles Darwin, Francis Galton, and the eugenics movement. This can involve biological patterns like fingerprints, facial geometry and patterns, eye retinas and irises, DNA, voice and body smells as well as behavioral traits like a persons manner of walking or travel patterns between physical locations. This biometric data is collected and used to represent, identify, and verify an individuals identity.
The FBI has developed a system called Next Generation Identification which has been designed to contain all of these types of biometric data including the millions of finger prints already on file and as many as 52 million faces by 2015. Importantly, this database blurs the boundary between data from convicted criminals and innocent citizens raising important privacy and civil rights concerns. When searching for a person in this system the resulting top 50 matches may only contain the correct person 85 percent of the time. This means that many innocent people will be presented as suspects for crimes in which they had no involvement.
Many private industries are also creating biometric databases with commercial applications open to the public. An example of which is FacialNetwork.com , which is a cloud based facial biometric database that developers are using to create mobile based recognition software for the public. Apps like theses will soon enable anyone with a mobile device to photograph someone and search the web for their identity and personal information.
However, it should be obvious that biometric data is not the only thing being collected. The United States and various multinational corporate entities are building an Orwellian police state with programs like PRISM , the successor to Total Information Awareness. These organizations collect and monitor nearly every piece of digital information communicated online today for government based surveillance purposes.
The implications these programs have on our privacy, identity and their impact on social interactions in the future is immense. They suggest a world in which we are always being seen, watched, and analyzed, and new algorithms will emerge ever rapidly which further leverage this data against us.
Data-masks have been developed in order to make these threats to our identities visible through illustrating the way these networked systems capture, classify, and represent human identity.
Process
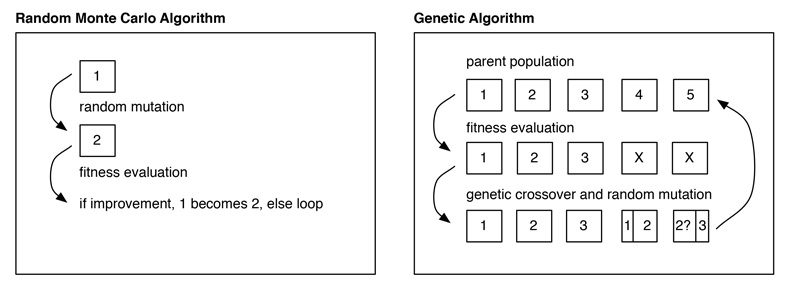
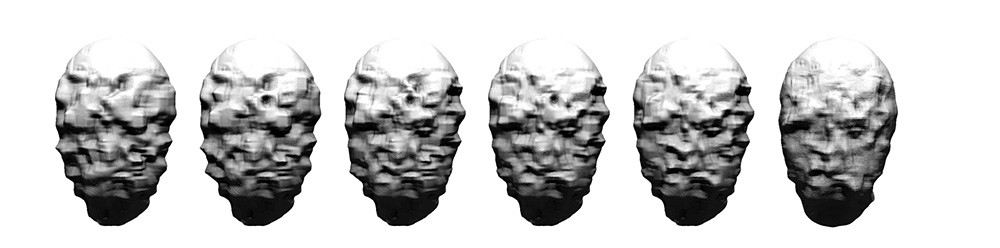
Stages of evolution for Chronos (Greco)
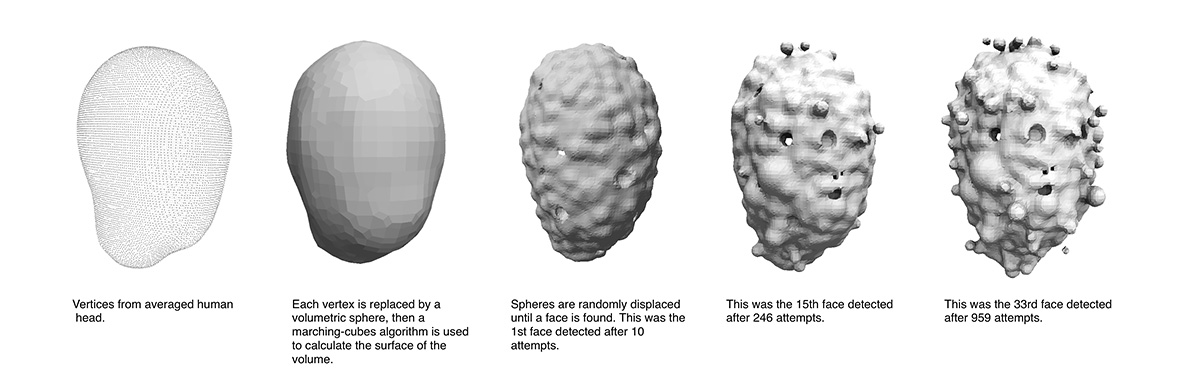
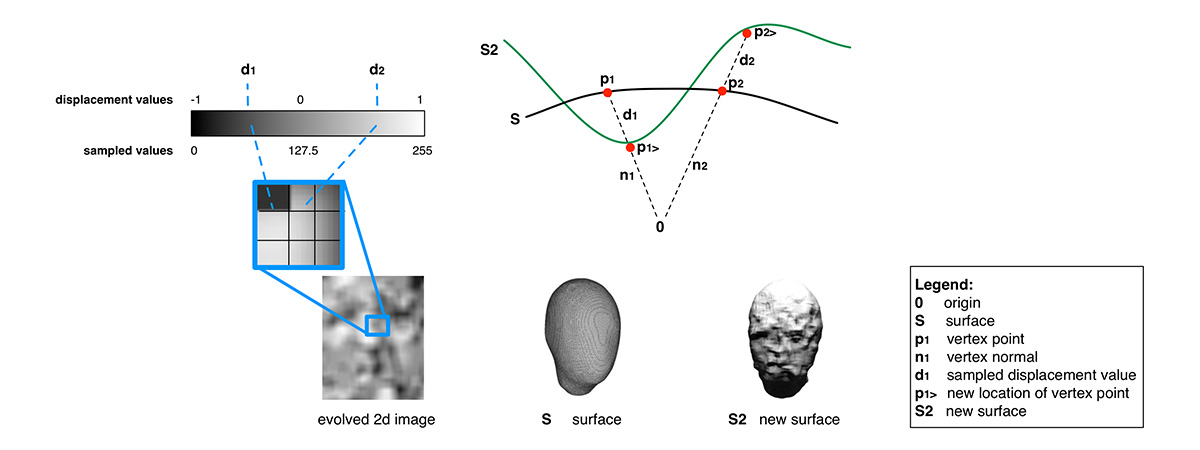
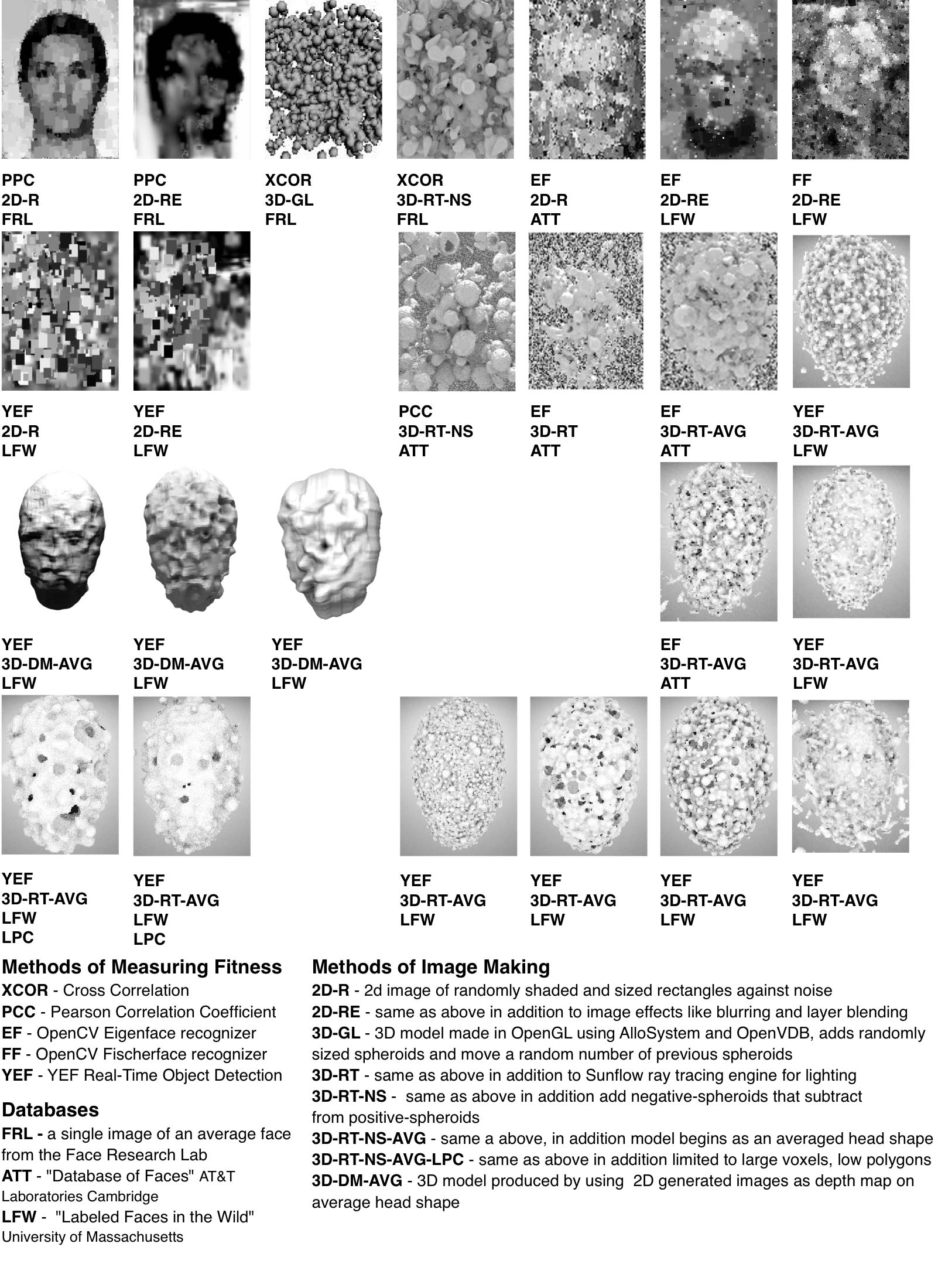
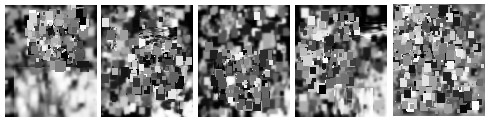
Links:
Facebook:
View active facial recognition of this work on FacebookGroup Exhibitions
The Face - Deutsches Hygiene-Museum, Dresden, Germany - August 2017.
Surveillance - The New Gallery, Calgary, Canada - Oct 2015.
GLOBALE: Infosphere - ZKM Karlsruhe, Karlsruhe Germany - Sep 2015.
Data Rush - Noorderlicht Photofestival, Groningen, Netherlands - Aug 2015.
CacheCache(Cache) - Gallery L'île, Paris, France - Jun 2015.
Faceless - De Marketen - Brussels, Belgium - Jan 2015.
in the context of the 8th edition of the Computers, Privacy & Data Protection Conference
Press:
Bomb Magazine "Interview: Sterling Crispin - Data Masks and The Technological Other." - Ben Valentine 2015Matter - Medium.com, "This Is What Your Face Looks Like to Facebook" - Kyle Chayka 2014
Y-Combinator Hacker News "Reverse-engineering facial recognition" 2014
Daily Dot, "Creepy masks show what your face looks like to Facebook" - Taylor Hatmaker 2014
Boing Boing, "Algorithmically evolved masks that appear as faces to facial-recognition software" - Cory Doctorow 2014
Wired Italy "Facebook ti vede così" - Dorothy Parlangeli 2014
Flowing Data "Detecting your face" 2014
Digi Today "Näinkö Facebook näkee kasvomme?" 2014
Suddeutsche.de "Wie Maschinen Menschen sehen" - Hakan Tanriverdi 2014
Fast Company "This Is Your Face to Facebook: Creepy Data Masks Show the Monstrous Side of Facial Recognition" - Jennifer Miller 2014